Comparison of ColdCard, Trezor, Ledger & Security Tips
Originally posted on the Veriphi blog (defunct) on June 7,2020.
Comparison of ColdCard, Trezor, Ledger & Security Tips
This is one article of many dedicated to help you along your journey to becoming a Sovereign individual for all things Bitcoin-related. Bitcoin’s value proposition has been discussed and vulgarized many times over so this won’t be the subject of this series. Instead, what we provide are the means to actually fully leverage what Bitcoin has to offer in terms of censorship-resistance, trustlesness, confiscation-resistance and verifiability.
We begin this series with the security basics. You can only truly transact bitcoins while benefiting from the properties mentioned above if they are under your control and only yours. This means that you must detain the private key tied to the funds displayed in the Bitcoin public address. Many alternatives exist, such as software wallets, you can see our analysis and recommendations here. However, this is not the most secure option to store your funds. If you only have a small amount and are just looking to dip your toes, this could be a temporary solution.
Using the Right Tools
A secure method to protect your keys first entails generating them using enough entropy. Read more about public key encryption in Bitcoin here. You could do this yourself, but unless you are well-versed in cryptography, it is not recommended. The easiest way to do so would be through the intermediary of a hardware wallet. Hardware wallets are really efficient and secure considering their low cost. However, if you have a significant amount of bitcoin you should consider additional security measures in order to be certain your funds are safe. If this is the case, drop me a line and I’d be more than happy to help figure out the best solution for you. I recommend the Coldcard hardware wallet, you’ll understand why by reading this article.
Hardware wallets are more secure than other methods to store your bitcoins since the private keys never leave the devices and are not transmitted to other computers. This means that both your private and public keys are handled separately with different sets of microprocessing chips. Most of the hardware wallets use a Secure Element, a special type of microprocessor. They are used in a variety of different devices that implicate payments, authentication and digital signatures. Unlike software wallets, that are more general-purpose, hardware wallets only serve one function: to hold your bitcoins securely.
Hardware wallets only have one purpose, and it’s to secure your bitcoins. The ones we talk about here have been constructed with limited interfaces and without any sort of general-purpose software. This is to limit the surfaces of attack and provide you with a reliable form of security for your bitcoins.
Most hardware wallets are open-source. This means the community can test them out and find malware, bugs and irregularities that may compromise the user’s security. On the other hand, open-source hardware wallets are vulnerable to having their internal logic reverse engineered and are easier to break into if they are physically accessible.
Since your keys never leave the hardware wallets, it is much more secure than holding your bitcoins on a mobile wallet and vastly more secure than keeping funds on an exchange.
There are multiple hardware wallets in the market, but this guide will solely focus on three of them: the Trezor (models One and T), the Ledger Nano S and the Coldcard.
These companies have been working in the industry for quite some time now and have demonstrated a certain amount of trustworthiness since they have been scrutinized by others in the field. The hardware wallets models mentioned above are a good starting point to choose from. Any other new hardware wallet product launched by an unknown company must first be thoroughly verified by independent experts, no matter how appealing their new device may look.
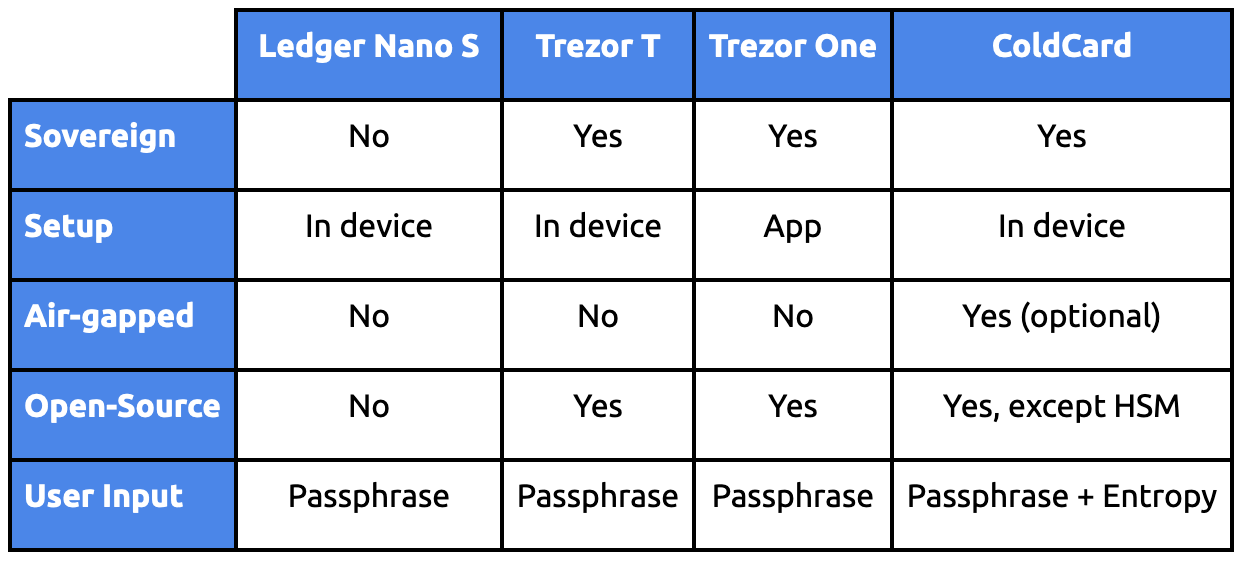
Here’s an overview of the wallets we will be discussing throughout our guides:
Why These Hardware Wallets?
Ledger and Trezor are by far the most popular brands on the market which means many users reading this article might have them. The Coldcard is the only credible hardware wallet that is fully air-gapped. This means the device never connects directly to a computer, since it can communicate through a microSD card. This helps avoid any link between your device and potential threats coming from an Internet connection. It is also the only credible hardware wallet that allows the user to generate their own entropy when creating your seed phrase thanks to a dice roll function.
The three models support multisignature schemes, they offer good privacy (except for the Ledger) and are compatible with Electrum Wallet, a fully open-source software.
How do Hardware Wallets Work?
They are physical devices which have the purpose of generating private keys and storing them on the same device. The private key never leaves the device but still allows for signatures and public keys to be shared with the adequate permissions.
When initializing your device, it will generate a 256-bit seed. This seed is usually deterministic, meaning that your wallet will contain private keys that are all derived from a common seed through the use of a one-way hash function. The BIP-32 standard, also known as a HD wallet, contains keys derived in a tree structure. A parent key can derive several children keys, which then can derive a sequence of other children keys. Thanks to this standard, you can create multiple public keys without having access to the corresponding private keys, so you can issue a different public key for each transaction, improving your security and privacy.
Source: https://github.com/bitcoinbook/bitcoinbook/blob/develop/ch05.asciidoc
The BIP-39 standard allows you to have a standardized way of displaying your private keys since, instead of having a string of random letters and numbers, you have a sequence of English words, selected from 2048 possible words, that your wallet displays for you to record with a pen and paper. This is crucially important since it is a mnemonic representation of your private keys. This can be used to recreate your seed and then recreate the wallet and all of its derived keys.
Source: https://github.com/bitcoinbook/bitcoinbook/blob/develop/ch05.asciidoc
It is not possible to guess or randomly generate these 24 words in their specific order. There are 256 bits of entropy, and each bit being either a 0 or a 1, you have 2256possibilities, or 115,792,089,237,316,195,423,570,985,008,687,907,853,269,984,665,640,564,039,457,584,007,913,129,639,936 possible combinations for the 24 words. This is like correctly guessing the position of an atom selected from the visible universe.
Added Security with a Passphrase
The BIP-39 standard also allows for an optional passphrase. When used, a stretching function produces a different seed from the same mnemonic. This means that different passphrases lead to different seeds, so you can have a vast set of possible wallets. A passphrase serves to improve your security, since the mnemonic phrase on its own is useless. Here is an illustration of the effect various passphrase lengths would have on the cost of an attacker brute forcing their way into your device.
It also allows you to have some sort of backup wallet which you could use under duress. Since using a passphrase leads to a different seed, you could redirect an attacker to a wallet containing a smaller amount of funds.
It is important to note that if the passphrase is lost or forgotten, so will the funds tied to that seed. You should also avoid storing your passphrase in the same location as your seed since it would defeat the purpose of having one in the first place.
Learn more about how a passphrase works in another article I’ve written, here.
The Basic Steps
The setup of a hardware wallet is composed of the following steps :
Unboxing and verification of package/receptacle integrity.
Selecting a PIN composed of only numbers which you’ll enter each time you want access.
Creating your private keys and backing it up as a seed phrase (24 words).
Selecting a passphrase (optional).
Upgrading the firmware to the latest version (the software running inside the device).
Linking a software wallet (in our guides it will be Electrum).
Receiving funds on the device by sending funds to an address displayed on the software wallet and/or the hardware wallet.
Risks and Threat Vectors
Acquiring your hardware wallet
After you have selected your desired hardware wallet, it is time to purchase it. You must make sure you are on the right website or an official vendor of the company. There have been cases of phishing where people bought a compromised hardware wallet and got their funds stolen. Never buy second-hand hardware wallets, they could’ve been tampered or can malfunction.
A hardware wallet doesn’t guarantee your security
Your funds can still be stolen even if you use a hardware wallet. If you misplace your 24 words and a malicious person finds them, no hardware wallet can protect your funds from getting stolen. If you don’t store them properly and they burn or the writing fades or you lose them, your funds are as good as gone. Follow the instructions carefully in order to minimize that risk. NEVER put your 24 words on an electronic device.
Other risks are much more complex and out of control of the regular users, however it is important to be aware of them and constantly be on the lookout for signs.
Insecure Random Number Generator: In each hardware wallet there is a component that creates the private keys, they use heavy cryptographic tools to create the needed entropy. However the methods employed are various and some of them are flawed. Some hardware wallets permit you to create your own entropy so you don’t have to depend on an electronic device.
Compromised shipping process: Someone could intercept the shipment of your hardware wallet. You can look for signs of tampering on the device’s packaging and carefully follow your order online to spot any oddities.
Imperfect Implementation: Even if a hardware wallet is on the market there are still flaws uncovered regularly. New bugs are discovered and companies have to release new and improved firmwares to fix these vulnerabilities. Make sure to update your firmware regularly in order to do so.
Vulnerabilities
The Ledger Nano S & the Coldcard use what is called a “Secure Element” in the device which is a microchip that acts like a vault and is considered a very secure form of technology. This technology has one major inconvenience, which is that it’s not fully open-source, so to a certain extent there are risks there, even though they are extremely limited.
The Ledger Nano S also has a major privacy issue which doesn’t affect the other devices. By default, all the hardware wallets have privacy issues because they connect to external servers. This can be fixed by using Electrum and connecting it to your own node. However, even though this can be done on Ledger as well, it requires installing a Bitcoin App inside the device and this can only be installed through their software that links to their servers and exposes your device identity to a certain extent.
Both Trezor models available are fully open-source, which is a positive point, since anyone can verify their code and could install everything from source. However, since the code is open and available for anyone to see, it opens a vulnerability that the devices with a “Secure Element” aren’t affected with.
It’s technically possible to extract a seed phrase (24 words) from a Trezor, without having the PIN. By having physical access to the device and connecting it to a computer and running decrypting software on it, one could do so. The decryption can be done under 5 minutes and requires only $100 worth of equipment. This is technically possible but requires access to the hacking software or advanced technical expertise to create the software, which is hard to come by. This is highly unlikely to happen and is unheard of having happened in real life scenarios. You can read more about this here. However, implementing a passphrase is a way to protect against this kind of attack.
All things considered, we recommend the Coldcard hardware wallet.